Introduction to Microsoft Office 365 Mobile Device Management (MDM)
In the past few years, with changes in the social environment and market ecology, coupled with the continuous impact of the new crown virus in the past six months, BYOD has become more and more popular.
Working from home gives colleagues in the industry more opportunities to use their own devices to access mailboxes. The file resources of the organization even involve files that are confidential or contain private information. While Bring Your Own Device (BYOD) provides convenience and flexibility, it also poses various challenges for organizations in device management and file data security. Therefore, it is not difficult to imagine that organizations need to consider formulating unified information security and management policies to further reduce management costs while providing a better user experience.
When talking about BYOD, I believe that many organizations also use Microsoft Office 365 solutions to handle their daily business. The following is a brief description of the MDM solutions and functions:
- Basic Mobility and Security
- Already included in each Office365 service plan
- Support Windows 10, iOS, Android and other mobile devices
- Restrict users to only use registered mobile devices to access mail and documents
- Improve account access security through Multi-Factor Authentication (MFA)
- Set up and manage mobile device security principles, such as detecting whether the device is cracked, locking the device, encrypting, and washing the machine remotely when the device is stolen, etc.
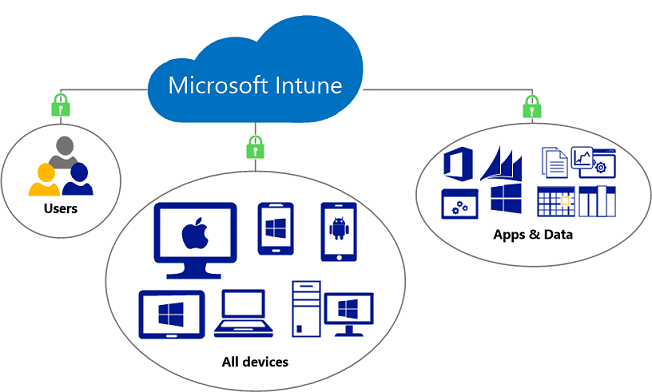
- Microsoft Intune
- Independent charging project and management platform
- Support Windows 10, iOS, Android, MacOS and other network settings
- Based on the Basic Mobility and Security function, additional powerful and flexible settings are provided
- Provide Conditional Access (Conditional Access) according to actual operating scenarios:
- Specify users or groups
- Restrict users to access only in specific areas or locations
- Restrict the use of designated devices and operable actions (such as copy, cut, paste, etc.)
- User attempts to log in to a specific app to trigger additional authentication
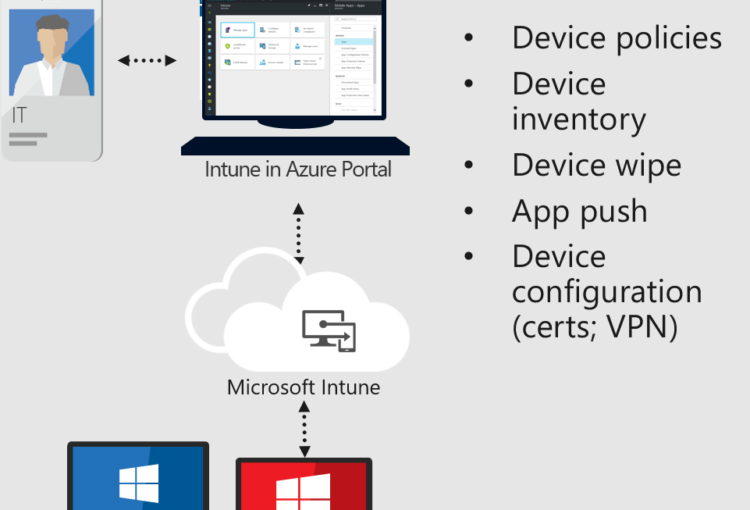
Reference URL: https://www.microsoft.com/en-us/microsoft-365/enterprise-mobility-security/microsoft-intune
If you have further inquiries about the functions of the above solutions or purchase authorization, please contact the Information Technology Resource Center (ITRC)
Phone: 2922 9280
Email: [email protected]
